Last week, I received quite a lot of really positive feedback for my first attempt at writing a digest. Thank you for that Kevin and Frederik, super kind of you! Even Payara picked it up.
One thing that I have changed this week is my iPhone home screen from which I removed the Twitter app (which I had on the first page). Instead, I put Music back into it. Also, trying to be more conscious about my time spent, I added the Apple time tracker:
Let’s see how that goes.
I started my weekend after traveling last week with… Not cycling but with this awesome video by Mary Spender:
If you didn’t watch it, it’s actually not about todays music not sucking, but against nostalgia holding things back. I liked it a lot, good stuff and actually pretty positive.
I finished reading Verschwörungsmythen by Michael Blume:
Very good read. I never thought about Platons allegory of the cave as something not that positive, but when you have a closer look, it can indeed be connected to conspiracy and the “charismatic” leaders leading the poor people out of the cave. And on the other hand, the red pill is indeed the entrance to the rabbit hole, but not in a good way.
While watching it I thought: “I should post this.” Why, actually? I am not a content / link creation machine and I just can refuse. Let thinks sink in a bit and see if they are worth sharing a week later anyway.
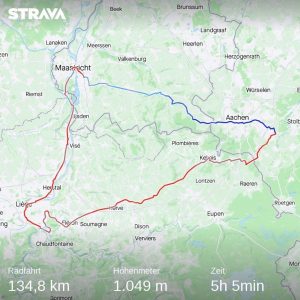
Before we jump a bit into Java: Of course I did cycle on the weekend and it’s madness. I was riding roughly 200km on both days in short/short. In freaking November. The map on the right: Yes, the track reassembles the temperature of one of those rides. Still, those rides give me as much serenity as the guy on the mural seems to have:
A bit related to that, my friend Markus wrote an excellent article about changing his habits at LinkedIn: Dieting vs. Nutrition vs. Rethinking my lifestyle. I’m very impressed by his achievements. I vividly remember our Devoxx 2019 conversation about that topic and role models and such: Chapeau, Markus. Well done. Wrt to nutrition: I’m still on the hard, fast and wrong side of things (apart alcohol) but that works well enough for me atm.
This week was Nodes 2022 and I worked liked crazy to get the documentation of Neo4j-Migrations into our labs pages: Neo4j Migrations Docs / Introduction. Together with Guillaume and Adam we used the existing AsciiDoctor documentation and are now building it with Antora. See the related commit. Antora makes it necessary to rethink a bunch of things, but I am totally in love with the fact that “my” build now notifies our docs repository and that in turn pulls my docs and integrates it into a bunch of other modules. Sweet stuff.
As preparation of his Nodes2022 talk, Gerrit put up a video about Testcontainers and integration testing:
I also did a presentation yesterday day and here are my slides about Neo4j-Migrations or what I call it, the lean way of refactoring Neo4j database content:
I am unsure how good my presentation was in the end: I realised with last weeks Øredev and yesterdays Nodes2022 that I am much better offline than on video. At least, this is how I perceive it.
Maciej was on fire this month with excellent posts about getting Tailwind CSS into Spring Boot proper (at some point, I will revisit my biking application and remove all that SPA Angular stuff and go back to SSR with Thymeleaf for my own sanity) and this is great stuff. He has a bunch of more things that I am using regularly, too, i.e. Activating Maven Profile by Operating System.
From Maciej and my colleague Gerrit comes 🚀 Introducing YOLO – because life is too short for running tests btw. Just click if you’re up for a laugh.
I expected this a bit later this year, but here it is: Spring Framework 6:
As a major revision of the core framework, Spring Framework 6.0 comes with a Java 17+ baseline and a move to Jakarta EE 9+ (in the jakarta namespace), with a focus on the recently released Jakarta EE 10 APIs such as Servlet 6.0 and JPA 3.1. […] Don’t be stuck on Java EE 8, make the leap to the jakarta namespace, ideally straight to the Jakarta EE 10 level! The upcoming Spring Boot 3.0.0 release includes corresponding managed dependencies for you.
IMHO this is quite big for the ecosystem. I cooperated with Heise Online a couple of weeks ago and so we did have a comment ready (in German): Spring Framework 6 verarbeitet Native Images und baut auf Jakarta EE 9 oder 10.
I did already share this article on Twitter, but it’s super interesting still. It’s about databases and query planning. Funny enough, the week before I hang out with Andres Taylor, one of the minds behind it. Andres is one of the original creators of Neo4j Cypher and was also involved in the Cypher-DSL before I took this over.
While Twitter seems indeed to be burning, I will dive into a bit of nostalgia as today, November 18th, a rerelease of Queens 1989 album “The Miracle” will happen, including a bunch of unreleased Queen demos. Looking very much forward to that: Was it all worth it?
Filed in English posts
|